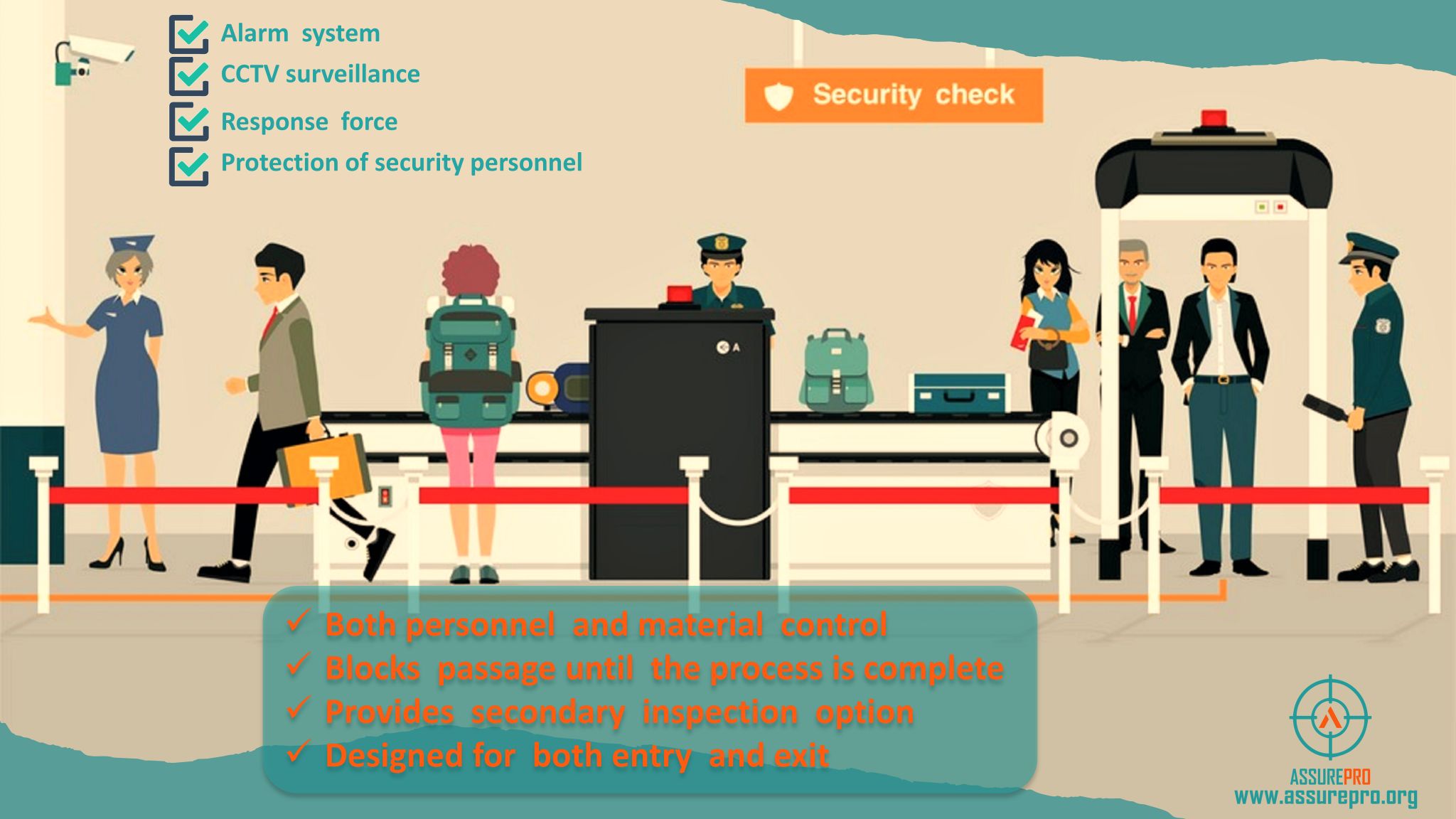
Security Supervision: Your Team Doesn’t Do What You Expect, They Do What You Inspect
In security operations, the phrase “Your team doesn’t do what you expect, they do what you inspect” underscores the critical need for hands-on supervision and engagement. Setting expectations alone is insufficient; security teams require continuous oversight, active involvement, and regular feedback to meet performance standards. Without structured accountability and supervision, even the most carefully designed … Read more